Introduction
Bots pose a significant threat to the integrity of phishing infrastructure, primarily by automating detection and countermeasures that can prematurely expose and neutralize simulated phishing campaigns. These automated agents can range from security scanners, which seek out and report phishing attempts, to malicious bots designed to flood systems with fake submissions, obscuring genuine interactions and skewing test results. For penetration testers and red team operators, the challenge is twofold: ensuring that our simulated phishing environments remain undetected for the duration of the test and maintaining the quality of data collected. By effectively mitigating bot interference, testers can ensure that their assessments accurately reflect how well an organization can withstand and respond to real-world phishing threats.
It is essential to have defense mechanisms in place to thwart off bots during your social engineering exercises. The previous way that EvilGophish would protect itself against bots was redirect rules and an IP address blacklist with Apache2 in front of the phishing infrastructure. You could define specific user agents, domain names, and IP addresses that would trigger an unauthorized request and redirect the client somewhere else away from the infrastructure. There is an obvious flaw with this methodology: everything is predefined. You cannot possibly prepare for every user agent that can potentially detect your infrastructure as phishing. The same goes for domain names and IP addresses. In comes Cloudflare Turnstile.
Defeating Bots with Cloudflare Turnstile
In the digital domain, where bots constantly evolve to mimic human interactions more convincingly, distinguishing between genuine users and automated entities is increasingly challenging. Cloudflare Turnstile emerges as a sophisticated solution in this context, designed to seamlessly differentiate between human users and bots without compromising the user experience with intrusive challenges.
Invisible Verification
At its core, Cloudflare Turnstile leverages advanced behavior analysis and anomaly detection techniques. Unlike traditional CAPTCHA systems that require users to solve puzzles or identify images, Turnstile operates quietly in the background. It analyzes interaction patterns and browser environment characteristics to assess the likelihood of a visitor being human.
Behavioral Analysis
Turnstile examines various aspects of user behavior, such as mouse movements, keystroke dynamics, and touch interactions. These subtle cues, which are challenging for bots to emulate convincingly, contribute to a risk score calculated for each visitor. By focusing on natural user interactions, Turnstile ensures that legitimate users are seldom, if ever, presented with a challenge.
Adaptive Challenges
When Turnstile encounters behavior that closely resembles bot activity, or when it can’t confidently distinguish a user as human, it may deploy lightweight, non-intrusive challenges as a secondary verification layer. These challenges are designed to be minimally disruptive, ensuring that even in cases where verification is required, user experience remains a top priority.
Continuous Learning
Leveraging the power of machine learning, Turnstile continuously refines its detection algorithms based on new data. This adaptive approach ensures that Turnstile remains effective against evolving bot tactics. By analyzing vast datasets and identifying emerging patterns associated with automated behaviors, Cloudflare ensures that Turnstile’s detection mechanisms are always up-to-date.
Privacy-centric Design
In today’s digital landscape, user privacy is paramount. Turnstile is engineered with a strong emphasis on privacy, ensuring that personal data is protected. By focusing on behavioral patterns rather than personal information, Turnstile provides a verification method that respects user privacy while maintaining security.
Cloudflare Turnstile Conclusion
Cloudflare Turnstile represents a significant advancement in the fight against bots, offering a user-friendly, privacy-conscious alternative to traditional CAPTCHAs. Its ability to operate invisibly, combined with the use of advanced behavioral analysis and adaptive challenges, ensures that bots are effectively thwarted while genuine users proceed unhindered. As phishing infrastructure becomes more sophisticated, tools like Turnstile are invaluable for maintaining the integrity of the infrastructure, ensuring that only real users can interact with it.
EvilGophish Tutorial
In order to provide this functionality, EvilGophish now comes with a HTTP server that listens locally on port 80 to process Cloudflare Turnstile challenge responses while the Evilginx proxy will proxy to this local server in order to carry out challenge response validation. A diagram of this infrastructure is shown below.

The first step is to create an account on Cloudflare, add a new site which will be your phishing domain, and retrieve the public/private keys.
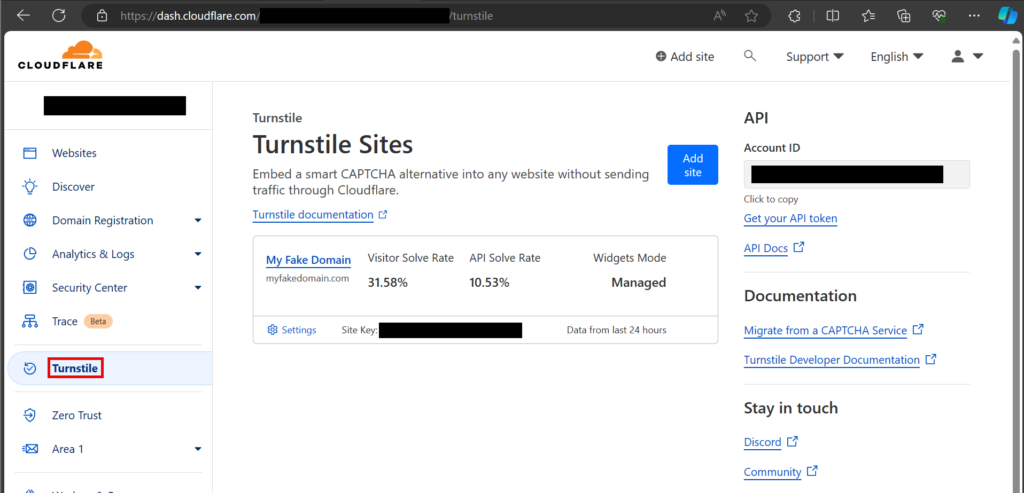
Once you have retrieved the public and private keys to validate Cloudflare Turnstile challenge responses, the next step is to create an HTML template for the Cloudflare Turnstile validation page. I have included a sample template in the EvilGophish repository which is shown below. I will not cover all of the template variables in-depth here as they are covered in the project’s README.md file.
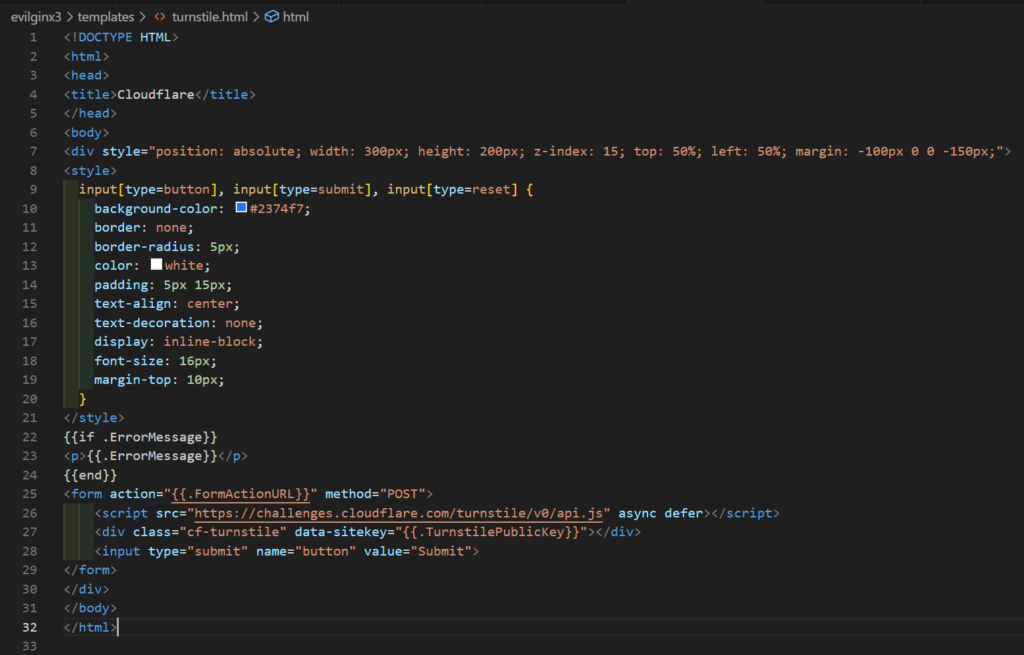
The use of Go HTML templates is to prevent static HTML code signatures in phishing infrastructure. It goes without saying that if you use the default template included in the project, you are likely going to get your infrastructure caught quickly. You are advised to change the template to include different code that has different styling and text. It also gives operators a lot of flexibility in how they would like to include this in their campaigns. You can make this fit together with your pretext by including logos that correspond with your phish, etc. There is also a template for forbidden responses that return a 403 code which is shown below.
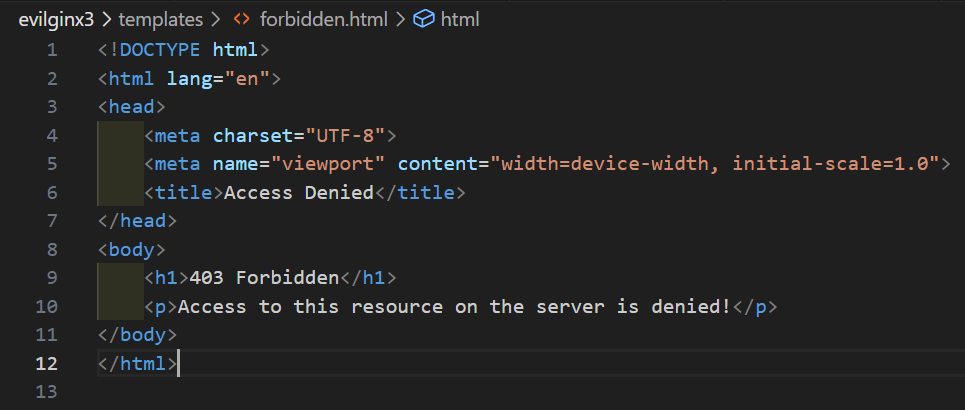
For all requests that do not have a valid session cookie from the Evilginx server (i.e. a request that doesn’t trigger the lure path), a 403 Forbidden response will be returned. A 403 Forbidden will also be returned if any errors occur during the Cloudflare Turnstile challenge response validation. This makes the infrastructure more malleable overall by being able to control this content as an operator. After you have your templates created and you are satisfied with them, you are ready to get going. The last step is to provide your Cloudflare Turnstile site keys to Evilginx and launch a campaign. I have included detailed instructions in the README.md of the project and have shown a similar command line below.
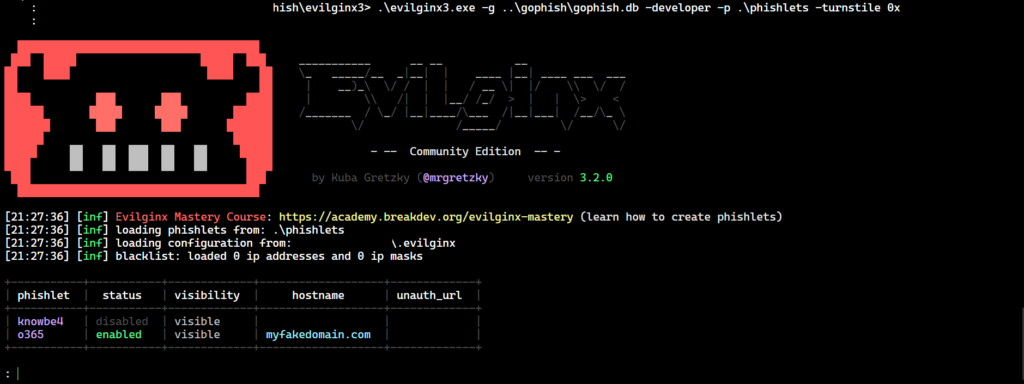
When you officially launch your campaign, you will see the HTML page you created for your template. I have shown the default template in action below.
Upon successfully completing a challenge, a victim will then be redirected to the Evilginx lure. If a client fails to complete the challenge, it will continue to display the Cloudflare Turnstile template page until a success occurs. If a success never happens, the same page will continue to be displayed and the client will never be granted access to the Evilginx lure. This forces the client to produce a successful challenge or access is never granted, hardening your phishing infrastructure against bots and other automated scanning software.
Conclusion
The escalating sophistication of bots presents a formidable challenge in cybersecurity, particularly when ensuring the integrity of systems designed to simulate or test phishing vulnerabilities. Traditional defenses often fall short, either by impeding user experience with cumbersome challenges or failing to accurately distinguish between human and automated threats. Cloudflare Turnstile represents a paradigm shift in this ongoing battle, offering a solution that balances robust security with user convenience.
By leveraging advanced behavior analysis, adaptive challenges, and continuous learning from interaction data, Turnstile provides an effective shield against bots, ensuring that only genuine users can interact with critical infrastructure. Its invisible verification process minimizes disruptions, allowing legitimate users to proceed unhindered, while still offering the option of minimal, non-intrusive challenges when necessary. This dual approach ensures that security does not come at the expense of accessibility.
For cybersecurity professionals and penetration testers/red team operators, integrating Cloudflare Turnstile into phishing infrastructure or similar testing environments underscores a commitment to cutting-edge security practices. It not only enhances the realism and effectiveness of simulations but also protects the integrity of these essential cybersecurity exercises. Turnstile’s ability to adapt to evolving threats, coupled with its privacy-conscious design, makes it an indispensable tool in the modern security toolkit.
Access EvilGophish here.
